Looks like my Interface design guidelines are required reading for a course in user interface design at the University of Baltimore.
Author Archives: admin
“An algorithm that is difficult to crack”
Type & Media in The Hague
Some of you already know that I took December and January off of work to finish up a portfolio of my typography and apply to the Type & Media Master program at the Royal Dutch Academy of Art in The Hague (Koninklijke Academie van Beeldende Kunsten, or KABK for short). You can read about a typical week there or about the history of the program. I flew out to the Netherlands last week to go to the KABK Open Day (Dag), be interviewed by the professors, and meet current and other prospective students.
Approximately eight billion people have demanded a blow-by-blow account, so here it is.
The city
The Hague is a city of about four hundred thousand people. The center of town is dotted with embassies and, like most European cities, crisscrossed by narrow cobblestone streets and filled with churches and buildings twice as old as the nation that I’m a citizen of.
Because of severe jet lag, I didn’t have much time to check out the city. But The Hague is home to Escher in Het Palais (Escher in The Palace), a fabulous museum with three floors of work by that original M.C., the Dutch artist and “intuitive mathematician” Maurits Cornelis Escher. You’ve probably seen Escher’s work in books and posters, but you haven’t really experienced it until you’ve seen it up close. Among others, they have prints of Three Worlds, Puddle, Tetrahedral Planetoid, and his masterpiece Snakes, made just months before he died.
The beach district of Scheveningen is a summer tourist destination. I took a trip out there on the tram (by the way, all of The Netherlands has a unified public transit system). It felt like a cross between Santa Cruz and Kowloon, a beach, boardwalk, and pier, with a few casinos, expensive restaurants and hotels (including the beautiful Kurhaus), and a string of shopping malls. There were lots of people out, including surfers, a group of about thirty pit-bulls and their owners walking on the beach together, and some sort of motorcycle show. I’m sure it’s a nice spot to get away to when it’s not 0˚C with a wind chill of -4˚C1.
The school
On Saturday I visited the school. Jan Willem Stas, the program director, and most of the current students were there to talk to. The typographers Erik van Blokland and Peter Verheul dispassionately listened to me present my portfolio and interviewed me. They conveyed no opinion either way about my work, and they were interviewing people all day long, so the best I can hope for is that I stood out a little bit. They are expecting about a hundred and twenty applications for a program that only takes eleven students each year, so the competition is steep.
I also met, briefly, Petr van Blokland, who teaches in the Graphic Design program at the school, and saw but did not get a chance to meet Paul van der Lans and Just van Rossum (yes, brother to Guido van Rossum), who also teach there.
I spent the rest of the time meeting and talking to the current students, and to a few of the other prospective students. My amateur typographic eye was extremely impressed with the quality of both the current and prospective students’ work. Several of the students had insightful, constructive criticism about my portfolio2, which was exciting and humbling. All of the students spoke very highly of the program and the professors.
KABK is also an undergraduate art school, and the entire school was participating in the open day. I toured the art/science, graphic design, industrial design, fine art, letterpress, photography, textiles/fashion design, and interactive media departments. I was impressed by all of it; It looks like a great environment. The letterpress students were letting people select a font—a real font, from a drawer, made out of lead—and print their names on the press. All the current Type & Media students were quick to inform me, however, that I’d be so busy with the Type & Media program that I wouldn’t have time to do anything else. Kinda like the first year of the Linguistics Master’s at UC Santa Cruz.
They plan to tell people in March, but the current students said I shouldn’t expect hear back from them until April or May, and one of this year’s students didn’t find out he’d been accepted until June. One student said the Dutch are very lax about deadlines and bureaucracy. That sounds refreshingly different from the academic system in the States, where everything revolves around filling out the correct paperwork in triplicate using a blue or black ballpoint pen and having it postmarked by the appropriate deadline, and if you screw up, you have to wait until next year.
Everyone was blown away that I flew from California to Europe just for the open day, but if I hadn’t flown out I would be applying completely blindly without knowing much about the program, the school, or the city. And I now know that the competition for the program is extremely tough, which helps me to be realistic about my chances (i.e. not great). While I have lots of friends who have a passing interest in typography, and while I’ve corresponded with other typographers online, I’d never actually met anyone else face-to-face who’d designed a typeface before. That alone made the trip worth it.
That didn’t take long
Following the Supreme Court’s decision to grant first amendment rights to corporations, Murray-Hill Incorporated is running for congress:
Stealing it back
Danny O’Brien sums up all the talk about the closed nature of the iPad/iPhone/iPod operating system perfectly:
But the truth is, the cyclical fight against locked-in systems has been the recurring theme of computing since the mainframes.
Get online as safely as possible while traveling
I’ve backpacked all over the world, and a friend embarking on a similar trip asked for my advice about how to stay safe when using internet cafés and youth hostel terminals. This advice might be helpful to other budget travelers, so here it is.
It’s important to understand that you’re putting yourself at significant risk every time you use a computer that’s not your own (and sometimes even when you’re using your own computer). The safest way to access the internet while traveling is to only use your own computer or smart phone. But budget travelers can’t always afford to carry a computer or a smart phone. The risk of theft of an expensive laptop or smart phone is much higher when traveling, especially when staying in shared rooms in hostels. And, as every backpacker knows, every single pound (or kilogram) you carry counts tenfold when you have to run a mile to catch a train. Traveling with your own, trusted internet device is often not feasible.
Another option is to just never go online while backpacking, but this often is not feasible either. The internet has become a tremendous source of tourist information plus an amazing tool to meet and coordinate with other travelers. And the long-term traveler must go online from time to time, to check their bank balances, pay off credit cards and mobile phone bills, and communicate with loved ones. The only alternative to this is the telephone, which requires staying up late or getting up early, and navigating an expensive and foreign telephone system.
All this adds up to the uncomfortable fact that you sometimes absolutely must get online in the next few days, and your options for doing so range from mildly to completely insecure.
The general idea is to first categorize your online activities by how secure they need to be, then, make an educated guess about the security of each computer you use, and use that as a guide for what you are willing to do online on that computer.
Step 1: Categorize your activities
Reading WikiTravel, finding hostels, or getting bus or train schedules doesn’t need a safe connection. If someone steals your password to a social network or CouchSurfing, the worst thing that can happen is that they use your account to say weird things to your friends, and you’ll have to reset your password or (worst-case) create a new account. Not that serious, in the great scheme of things. This, of course, assumes that you use different passwords for your different accounts, which is a good idea.
Checking your email needs to be a bit more secure, since with access to your email, anyone can impersonate you or steal your accounts on sites that use that email address. And lastly, making reservations with a credit card or logging in to your online banking are high risk, since with your credit card or bank details, you can be out of a chunk of money quickly.
Step 2: Categorize the available computer
Since I’ve never seen a single internet café running anything but Windows1, and since I’ve seen only one youth hostel with Linux computers2, I’ll only talk about judging the security of Windows computers.
The more professional internet cafés and hostel computers require you to log in, and usually you can tell if you’ve been logged in to a temporary, sandbox account, or if it’s the same account that every user gets logged into. If it’s the same account that every user uses, you’ll see personal files left on the desktop, in the trash, in the documents folder, and in the browser you’ll see browsing history and bookmarks and toolbars and plugins installed, etc, etc. If it’s a sand-boxed account, it should look like a pristine, clean install of Windows.
If it’s a Windows computer that you can just sit down at, don’t trust it. If there’s lots of random software visibly installed and files lying around, this means it hasn’t even been cleaned up recently. Use it to do research, but don’t type your passwords on it, and certainly don’t ever log in to online banking or type in your credit card details.
Sandbox accounts are much less likely to have malware installed, because only the owners/administrators, or someone who used an exploit to get administrator access, could have installed malware. If it’s sand-boxed, I generally feel ok logging in to my email, but I’m still wary about using it to log on to my online banking. In a pinch you could use Mint just to check bank balances, since it has read-only access to your financial information. Oftentimes I find myself making hostel reservations with my credit card on computers like this, but I’m never very happy about it.
Then there are places like EasyInternet, where users don’t have access to the filesystem, CD drive, or USB ports, you’re not allowed to download and run any programs, and where the entire Windows installation–not just the user account–appears to be wiped over the network each time the user is logged out. You can tell that the entire Windows OS is being wiped because the computer reboots as soon as you log out, and the startup process indicates that it’s booting over the network. These kinds of computers are the safest. These are the only places where I feel comfortable logging in to my online banking. There’s still a chance that someone administering the café is capturing your passwords, but there are probably only a few people who have enough authority to do so.
I also judge hostel computers to be more secure than internet cafés. Internet cafés are open to the general public, including locals who would have the time, and the motivation, to regularly visit the café, install malware, gather collected data. Hostel computers are generally just used by hostel visitors, which would mean a traveler installing malware would have much less time to install and troubleshoot the data-collection process, no chance to reinstall it when it gets removed, and they’d have to gather the collected data remotely. You still have to worry about a member of the hostel staff installing something malicious, but again, there’s fewer staff members, so a smaller chance that it’s been compromised.
If the computer has Firefox3 installed, I usually take that as an indication that they aren’t total morons about security. Even better if it’s set to the default browser. Installing Firefox yourself, and using it, protects you against malware in Internet Explorer, but not against malware installed on the system.
If you know anything about Windows, you could check the version of Windows it’s running and see how recently it’s had security updates installed, which would give you an even better idea how security conscious the administrators are.
Other tips
If you can’t get to a secure computer and absolutely must access your bank account, most ATMs will let you check your balance and make transfers (and watch out for ATM skimmers). And staying up late or getting up early to call your bank, while a hassle, is much better than finding yourself stuck in a foreign country with cancelled credit cards and not much cash.
Always make sure you’re using SSL. If your bank doesn’t use SSL, switch to one that does. Gmail and most of the other major email providers allow you to log in using SSL. Use it. Don’t make credit card reservations if the site doesn’t support SSL. And don’t do any of this if the browser on the computer you’re using doesn’t support SSL.
The last step in staying secure while traveling is to change all your passwords and pin numbers as soon as you are back at your home computer again. That way, if anything did leak, it’s rendered useless.
Those are my white-hat, benevolent-hacker notes about internet while traveling. Soon, I’ll post some true black-hat tales of hacking internet café to get free, or cheap, internet.
- No love for Mac OS X. [↩]
- High praise for Hostel Ruthensteiner, Vienna, Austria, running some sort of sand-boxed KDE, and where I felt almost as safe as on my home computer. [↩]
- I’ve never seen Safari or Opera in the wild, and Chrome was released after my most recent trip. [↩]
The wrong way to fix the electoral college
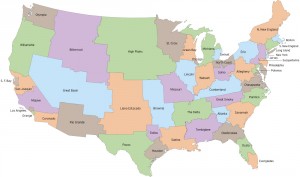
Neil Freeman’s recent Electoral College Reform map:
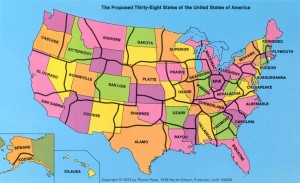
is reminiscent of C. Etzel Pearcy’s 1973 Thirty-Eight states of America:
Both suffer from a problem that the National Popular Vote plan doesn’t have: what happens when the population distribution changes?
You are what you buy
On Black Friday, artist Michele Pred “shop-dropped” prints of her artwork at Ikea. The prints are barcodes, which, when scanned, read “You are what you buy.” Ikea ends up with unexplained extra cash on their books, and a bunch of unsuspecting people have art hanging on their walls that’s both making fun of consumer culture, and worth a whole lot more than they think.
Visualizing the evolution of open-source projects
Here are two nifty visualizations of the evolution of open-source projects:
Exit through the gift shop
When Banksy makes a film, even I will play the viral video game:
Looks like Jackass crossed with Wild Style. One thing, though. Helvetica? How could a world renowned artisté such as Banksy stoop so low?